Understanding OAuth 1.0 and OAuth 2.0: A Comprehensive Overview
As the landscape of internet security evolves, OAuth has become a vital protocol for authorization. This article explores OAuth 1.0 and OAuth 2.0, examining their definitions, types of authorization, applications, and guidelines for selecting the appropriate protocol for your API.

What is OAuth 1.0?
Launched in 2007, OAuth 1.0 is an authorization framework that allows third-party applications to access user resources without exposing their credentials. This is achieved through the issuance of short-lived access tokens, with each API request requiring a cryptographic signature to ensure the integrity and authenticity of the request.
Key Features of OAuth 1.0
Delegated Access: Users can grant third-party applications limited access to their resources hosted on a service provider (often a website or platform) without sharing their passwords.
Authorization Types: The primary mechanism is three-legged authorization, where the resource owner must approve the access request.
Advantages of OAuth 1.0
Improved User Experience: Users can access resources across different platforms without creating multiple accounts.
Enhanced Security: The separation of user credentials from the authorization process reduces the risk of exposing sensitive information.
Standardization: OAuth 1.0 provides a uniform approach to authorization, promoting interoperability between applications and service providers.
What is OAuth 2.0?
Released in 2012, OAuth 2.0 is a more flexible and streamlined authorization framework designed to address the complexities of OAuth 1.0. It enables users to grant third-party applications secure and efficient access to their resources without needing to share passwords.
Key Features of OAuth 2.0
OAuth 2.0 allows various authorization types, including:
Authorization Code Grant: Suited for server-side applications where an authorization code is provided post-login.
Implicit Grant: Best for client-side applications, such as single-page apps (SPAs).
Resource Owner Password Credentials Grant: For trusted applications that collect user credentials directly.
Client Credentials Grant: For machine-to-machine communications without user context.
Advantages of OAuth 2.0
OAuth 2.0 has become the preferred authorization protocol due to several key benefits:
Simplicity: The streamlined process makes it easier to implement with multiple authorization types that suit various applications.
Enhanced Security: By eliminating the need for shared secrets between clients and resource servers, it reduces vulnerabilities. Token-based security with short-lived access tokens improves overall security.
Improved Scalability: OAuth 2.0 supports managing multiple client applications more easily, eliminating the need for complex shared secret management.
Flexibility: A wider range of grant types caters to diverse application requirements.
Mobile Compatibility: Tailored for mobile applications, OAuth 2.0 provides secure, token-based access, allowing users to access resources seamlessly across platforms.
Widespread Adoption: Major service providers like Google, Facebook, and Twitter widely implement OAuth 2.0, ensuring consistent user experiences across different platforms.
Application Scenarios
OAuth 1.0
Despite being less commonly used today, OAuth 1.0 remains relevant in legacy systems and certain early social media platforms where secure access to user data is necessary.
OAuth 2.0
OAuth 2.0 is the preferred choice for modern applications, supporting a broad range of use cases including mobile apps, web services, and API access. It enables functionalities such as single sign-on (SSO) and third-party integrations.
Reasons for the Development of OAuth 2.0
OAuth 2.0 arose to alleviate the limitations of OAuth 1.0, primarily:
Complex Implementation: The multi-step process and use of temporary tokens in OAuth 1.0 complicated deployment.
Scalability Challenges: Maintaining multiple shared secrets for various client applications proved inefficient as the web ecosystem expanded.
Security Vulnerabilities: Dependence on shared secrets heightened the risks of security breaches. The exposure of OAuth 1.0 tokens also posed challenges.
OAuth 2.0 simplifies authorization while enhancing security and scalability by:
Streamlined Authorization: Offering flexible authorization types improves adaptability to various use cases.
Reduction of Shared Secrets: This is achieved through the use of access tokens and public/private key encryption.
Improved Token Management: Introduction of limited-lifetime access tokens and refresh tokens enhances security and manageability.
OAuth 1.0 vs. OAuth 2.0
| Feature | OAuth 1.0 | OAuth 2.0 |
| Authorization Flow | Complex, with multiple steps and temporary tokens | Simplified, offering various grant types based on the scenario |
| Security | Depends on shared secrets (vulnerabilities) | Eliminates shared secrets, using access tokens and refresh tokens with limited lifetimes |
| Scalability | Difficult to manage multiple shared secrets | More scalable through public/private key encryption |
| Flexibility | Limited grant types | Broad range of grant types for different applications |
| Mobile Compatibility | Less suitable for mobile applications | Very suitable for mobile apps with token-based access |
| Adoption | Less widely adopted | Broadly adopted by major service providers |
| Focus | Secure access through complex handshakes | Simplified, secure, and flexible authorization |
| Ideal Use Cases | Legacy applications with complex access control | Modern web and mobile applications covering diverse scenarios |
Choosing the Right OAuth Version
When deciding between OAuth 1.0 and OAuth 2.0 for your API, consider:
Security Requirements: OAuth 2.0 implements advanced security practices, including token expiry and refresh tokens.
Complexity: OAuth 2.0 offers a simpler implementation, avoiding the complicated signing processes of OAuth 1.0.
Application Type: Determine whether your application is web-based, mobile, or machine-based to guide the choice of authorization method.
Implementing OAuth with EchoAPI
EchoAPI allows users to choose their preferred authentication method, whether OAuth 1.0, OAuth 2.0, or other types. This flexibility ensures developers can implement the solution that best fits their needs.
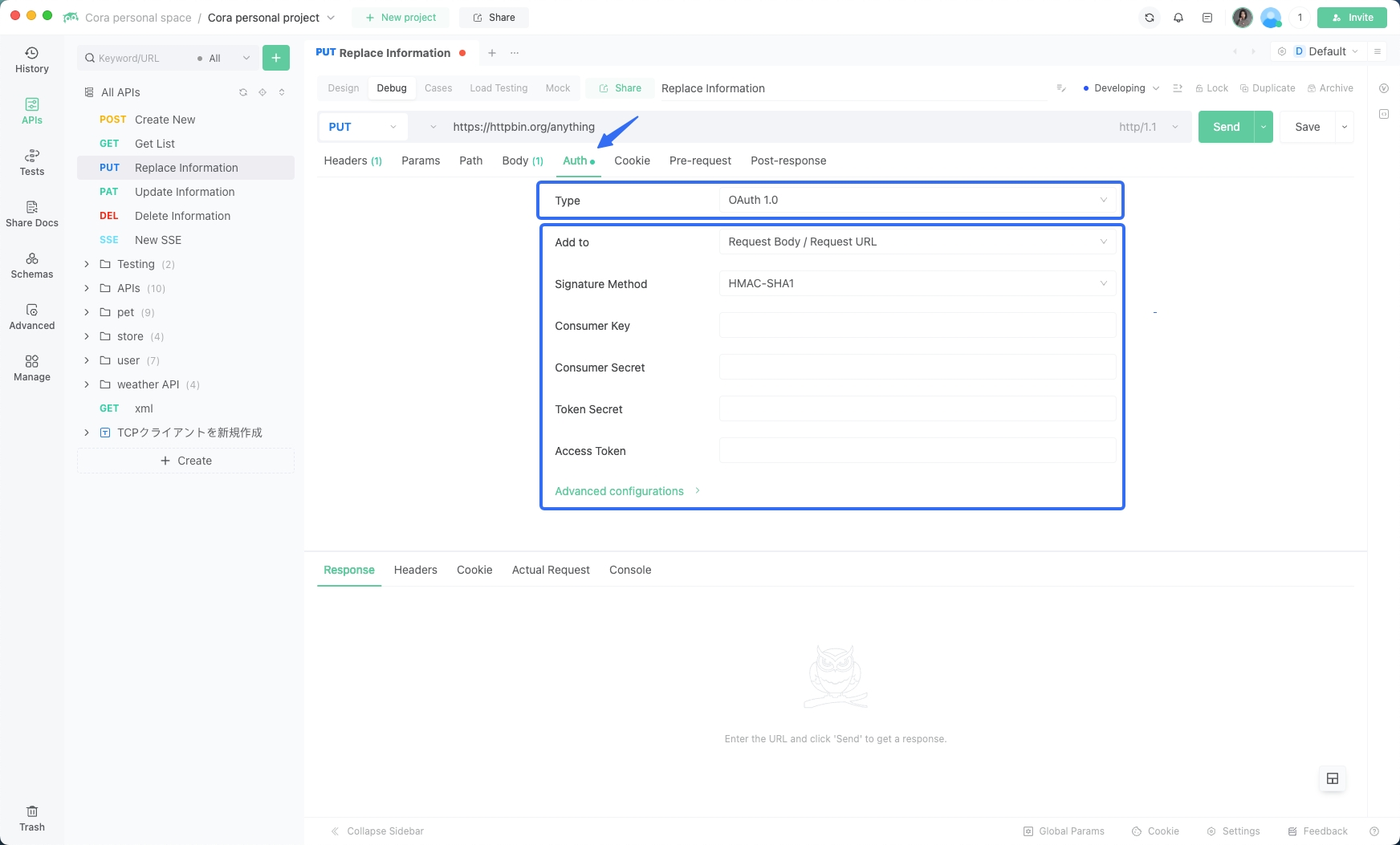
Using EchoAPI for OAuth 1.0 Authentication
To authenticate using OAuth 1.0 in EchoAPI:
1. Set the consumer key and consumer secret in the API settings.
2. Define the token parameters, including request token and access token.
3. Follow the redirect process to obtain user authorization.
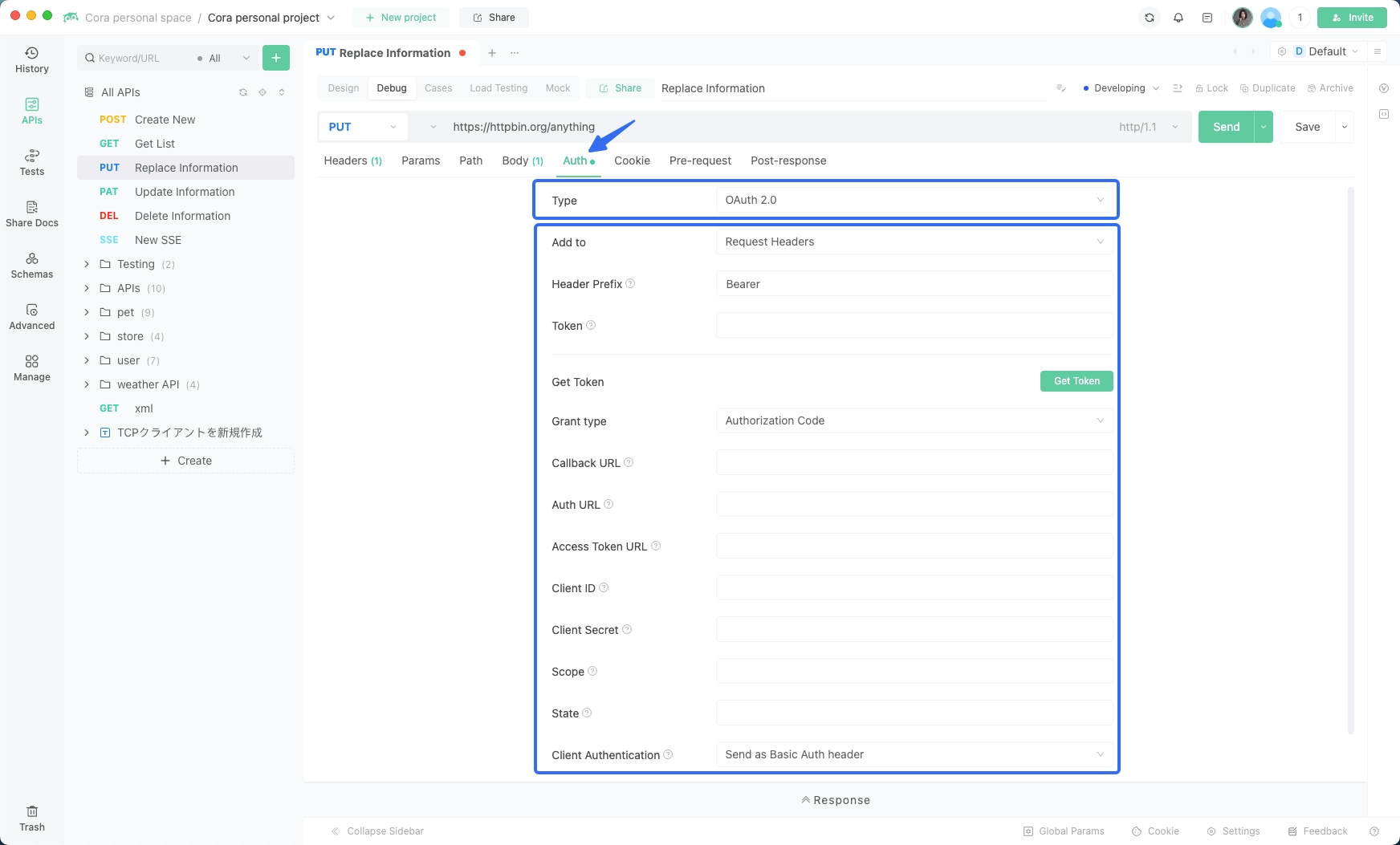
Using EchoAPI for OAuth 2.0 Authentication
For OAuth 2.0 implementation:
1. Create a new API request within EchoAPI.
2. Navigate to the Auth tab and select OAuth 2.0.
3. Enter your authorization URL, token URL, client ID, and client secret.
4. Save the configuration and begin testing your API with the generated access token.
Conclusion
OAuth 2.0 has established itself as the industry standard for secure authorization, offering improved flexibility and security over OAuth 1.0. Understanding both protocols is essential for developers aiming to implement secure and efficient access control in their applications. By leveraging tools like EchoAPI, you can seamlessly integrate the right OAuth approach to enhance the security and usability of your APIs—ultimately leading to a better user experience in today's interconnected digital landscape.
Try EchoAPI Interceptor today!