Securing REST APIs: A Comprehensive Guide to NTLM Authentication
In the world of cloud computing, Amazon Web Services (AWS) stands out as a leading platform that empowers developers and businesses to build scalable applications. A crucial aspect of interacting with AWS services via REST APIs is the AWS Signature, a method that ensures secure and authenticated communication between clients and AWS. Understanding how to properly implement and debug AWS Signatures is essential for anyone looking to make the most of AWS.
This guide will delve into what AWS Signature is, its importance in securing API requests, and provide practical tips on debugging it using various code examples and tools. Whether you’re a seasoned developer or just starting your journey with AWS, grasping these concepts will significantly enhance your ability to work with REST APIs effectively.
Why Use NTLM Authentication for REST APIs
As organizations increasingly rely on REST APIs to facilitate communication between services, securing these interfaces has become essential.

NTLM (NT LAN Manager) Authentication offers several significant benefits for API security:
Enhanced Security:
NTLM uses a challenge-response mechanism to enhance security by ensuring that credentials are not transmitted in plaintext, making it more secure than basic authentication methods.
Seamless Integration with Windows Environments:
Many enterprises operate within Windows-based networks where NTLM is already a standard protocol. Using NTLM enables easier integration with existing authentication systems.
User Credentials Management:
NTLM streamlines user credential management, enabling single sign-on (SSO), which reduces the need for users to repeatedly enter their credentials.
Support for Legacy Systems:
Organizations with legacy applications can adopt NTLM for API interactions without needing extensive overhauls.
What Is NTLM Authentication ?
NTLM Authentication is an iteration of the traditional NTLM protocol, optimized for modern RESTful API environments. This version retains NTLM's core functionality while improving its compatibility with modern web standards.
Key Features:
Robust Authentication Process:
NTLM uses a multi-round authentication process to ensure each request is properly validated.
Credential Protection:
By employing a challenge-response mechanism, NTLM safeguards user credentials from unauthorized access.
Web-Friendly:
The latest version is designed specifically for web applications, offering better support for modern API features and standards.
How to Implement NTLM Authentication in Java and Go
Java Implementation
To work with NTLM Authentication in Java, you can use the Apache HttpClient library. Here’s how you can implement it:
import org.apache.http.auth.AuthScope;
import org.apache.http.auth.NTCredentials;
import org.apache.http.client.methods.HttpGet;
import org.apache.http.impl.client.CloseableHttpClient;
import org.apache.http.impl.client.HttpClients;
import org.apache.http.impl.auth.NTLMSchemeFactory;
import org.apache.http.client.methods.CloseableHttpResponse;
public class NTLMJavaExample {
public static void main(String[] args) {
try (CloseableHttpClient client = HttpClients.custom()
.setSSLSocketFactory(new NTLMSchemeFactory())
.build()) {
NTCredentials credentials = new NTCredentials("username", "password", "workstation", "domain");
client.getCredentialsProvider().setCredentials(AuthScope.ANY, credentials);
HttpGet request = new HttpGet("https://api.example.com/resource");
CloseableHttpResponse response = client.execute(request);
System.out.println("Response Code: " + response.getStatusLine().getStatusCode());
} catch (Exception e) {
e.printStackTrace();
}
}
}
Go Implementation
In Go, you can utilize the http package along with an NTLM library to implement NTLM authentication. Here’s a simple example:
package main
import (
"fmt"
"net/http"
"github.com/Azure/go-ntlmssp"
)
func main() {
client := &http.Client{
Transport: ntlmssp.Negotiator{RoundTripper: http.DefaultTransport},
}
req, err := http.NewRequest("GET", "https://api.example.com/resource", nil)
if err != nil {
fmt.Println(err)
return
}
req.SetBasicAuth("username", "password")
resp, err := client.Do(req)
if err != nil {
fmt.Println(err)
return
}
defer resp.Body.Close()
fmt.Println("Response Code:", resp.Status)
}
How to Use Tools to Test NTLM Authentication
Testing the robustness of your NTLM Authentication implementation is crucial. You can utilize tools like EchoAPI,Postman or curl to perform this testing.
Testing with EchoAPI
Setup Request:
Create a new request in EchoAPI.
Choose the appropriate HTTP method (GET, POST, etc.) and enter your API endpoint.
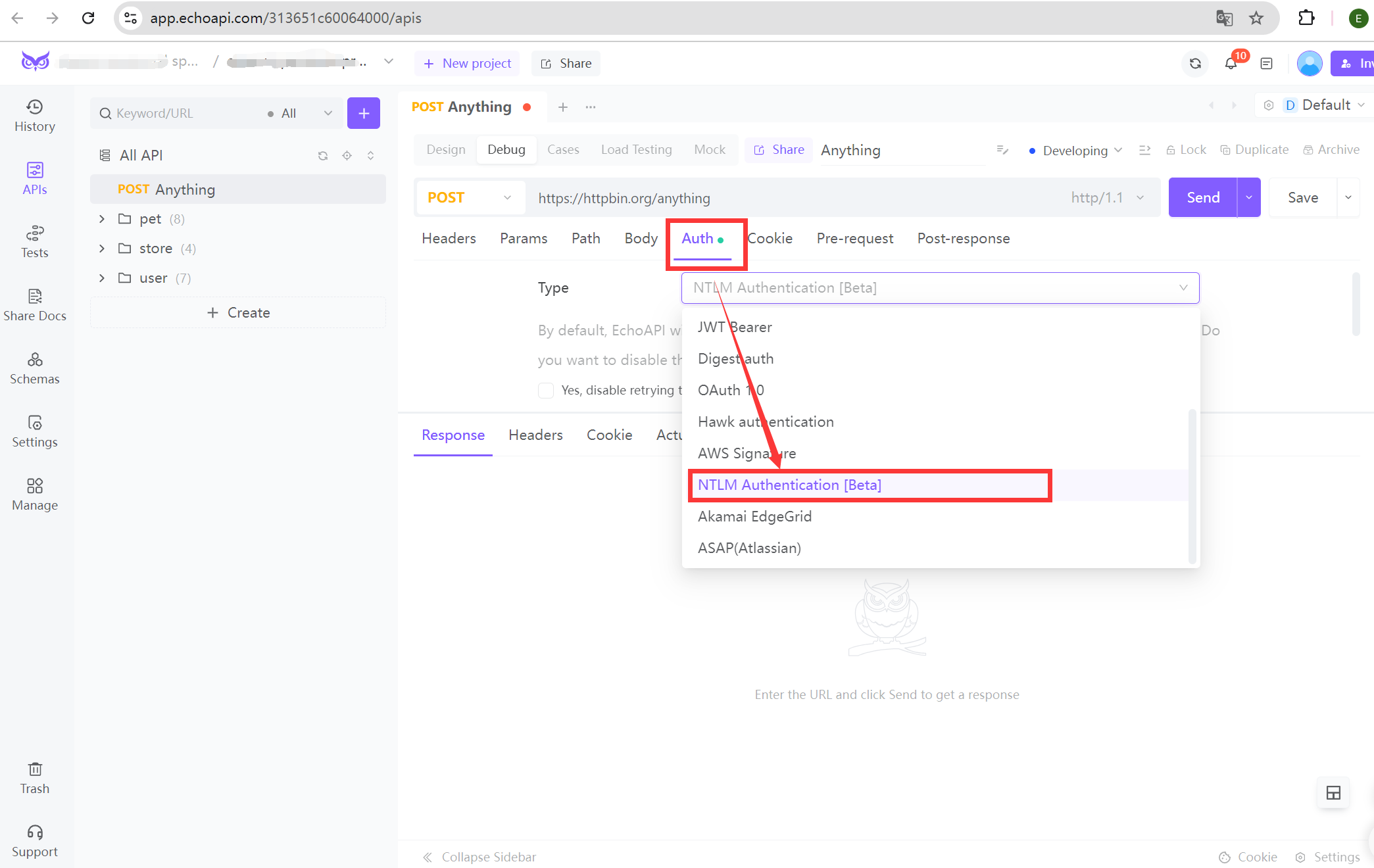
Authorization:
Navigate to the 'Auth'(Authorization) tab.
Select "NTLM Authentication" from the Type dropdown.
Input your domain, username, and password.
Send Request:
- Click "Send" to execute the request. Check the response to confirm successful authentication.
Conclusion
NTLM Authentication presents a robust and flexible solution for securing REST APIs, especially in Windows-centric environments. With easy implementations in Java and Go, along with tools for effective testing, developers can confidently enhance the security of their APIs. As API services continue to proliferate, adopting advanced authentication methods like NTLM will be crucial in maintaining the integrity and security of digital communications.
Try EchoAPI for VS Code today!